Hybrid is the destination, not the detour
For years, hybrid cloud carried a whiff of indecision, positioned as something you did while figuring out your “real” cloud strategy before committing fully to public cloud. That perception has shifted dramatically.
Gartner projects that 90% of organizations will adopt a hybrid cloud approach through 2027, which isn’t a prediction about companies stuck in limbo but rather a recognition that hybrid has become the dominant architecture because different workloads genuinely have different requirements.
Some applications need the elasticity of public cloud, while others need the performance of running close to your data center. Some data has to stay in specific locations for compliance reasons, while other workloads need to burst into cloud capacity during peak demand and pull back when things quiet down. Forcing everything into one box was never the right answer, and organizations have stopped pretending otherwise.
The more interesting shift is in the conversation itself, which has moved from “cloud or not” to “how do we secure the bridge between environments,” and that’s where most organizations are struggling.
The security conversation has been backwards
We’ve spent years debating whether cloud is “more secure” or “less secure” than on-premises infrastructure, with entire vendor pitches and countless conference panels built around this framing, but the framing itself misses the point.
According to Gartner, over 99% of cloud security failures are due to preventable misconfigurations rather than flaws in the underlying cloud platform. The platform isn’t failing these organizations. Configuration mistakes, credential sprawl, inconsistent policies, and governance gaps are where breaches happen.
The numbers get worse when you look at hybrid environments specifically, where research shows that 82% of breaches are attributed to lack of visibility. When security teams can’t see across both their cloud and data center infrastructure, they can’t protect it, and the handoff points between environments become blind spots that eventually become entry points.
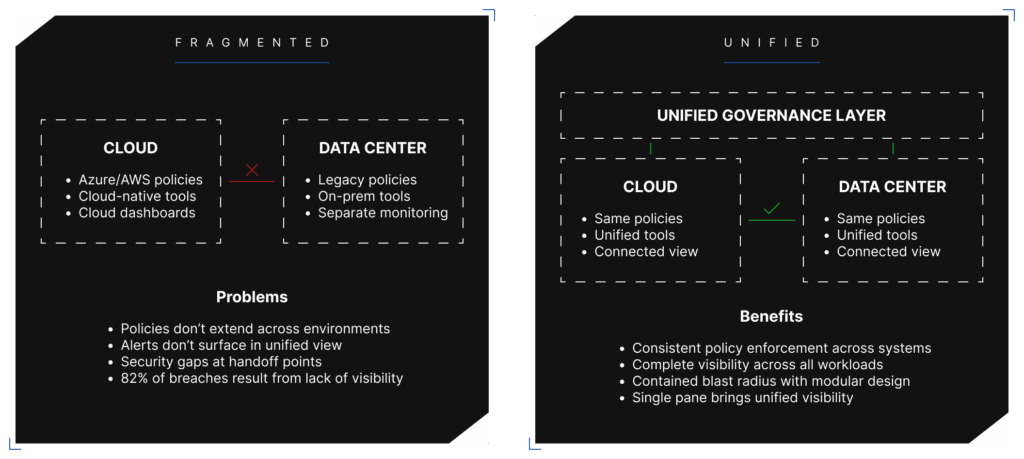
The real risk isn’t a question of cloud versus on-prem but rather fragmented governance: different policies for different environments, security tools that work in one place but not another, standards that apply to your Azure subscription but not to the workloads sitting in your data center. That fragmentation is where attackers find their openings.
Where the bridge breaks down
When your cloud and data center operate under different policy sets, the seams between them become vulnerabilities.
Consider how this plays out operationally. Your cloud environment has one set of access controls enforced through Azure policies or AWS config rules, while your data center has another set managed through different tools by a different team. Data moves between these environments constantly as backups replicate, applications call APIs across the boundary, and users authenticate from both sides, and every one of those handoff points creates an opportunity for something to go wrong.
The failure patterns tend to be predictable: security tools that don’t communicate across environments so alerts in one system never surface in another, policies that apply to cloud workloads but don’t extend to the VMs running in your colo, and visibility that stops at the data center door and leaves you blind to what happens once data crosses that threshold.
Most of the major cloud security incidents you read about trace back to these fundamentals rather than sophisticated zero-day exploits or nation-state attackers with unlimited resources. Somebody misconfigured a storage bucket, credentials got overprovisioned, or a third-party vendor didn’t follow the same standards as the internal team.
The companies getting breached aren’t necessarily doing anything exotic wrong; they just can’t enforce control consistently across their entire environment, and in a hybrid world, “entire environment” means both sides of the bridge.
What a secure hybrid posture actually requires
If fragmented governance is the problem, unified governance is the answer, though the concept sounds more straightforward than it is in practice, where it requires discipline and architecture that most organizations haven’t built yet.
The foundation is one governance model that applies everywhere, with the same policies enforced whether a workload runs in Azure, AWS, or your data center, and no exceptions for “legacy systems” or drift because one environment happens to be managed by a different team. If a security control matters, it has to matter everywhere.
Policy enforcement also has to happen through automation rather than manual oversight because you can’t rely on people remembering to do the right thing when environments are dynamic and teams are stretched thin. Every organization says they have policies, but fewer can prove those policies are enforced, and the difference comes down to whether governance is baked into the infrastructure or bolted on as an afterthought. When policies are defined as code and enforced automatically, you remove the dependency on manual compliance.
Visibility has to span the entire environment as well, with security teams able to see cloud and data center workloads in the same pane using the same alerting, reporting, and investigation capabilities. If understanding your exposure requires toggling between three different dashboards, you’re working with a fragmented picture that will always have gaps.
Architecture matters too, particularly blast radius control, which means building modularity into your environment so that a misconfiguration in one place doesn’t cascade everywhere. When you treat every subscription, every account, and every stack as an individual object with defined boundaries, you contain the damage when something goes wrong, and something always goes wrong eventually.
None of this is revolutionary since these are the same principles that have guided secure infrastructure for decades. The challenge in hybrid environments is applying them consistently across two worlds that often evolved separately with different tooling, different teams, and different assumptions about how security works.
Who this is built for
Not every organization needs to think this hard about hybrid security. Cloud-native startups with no data center footprint don’t have this problem, and massive enterprises with dedicated cloud security teams for each platform probably have it covered already. But there’s a large middle ground where this conversation matters a lot.
Companies with significant data center investments fall into this category, whether they’re running IBM workloads that process batch jobs against storage arrays that need to stay close to the compute, performance-sensitive applications where the latency to public cloud creates unacceptable delays, or two decades of infrastructure investment that isn’t getting ripped out anytime soon. These organizations need cloud capabilities while keeping one foot planted where it is.
Regulated industries face similar pressures, including healthcare organizations under HIPAA, financial services firms dealing with SOX and PCI, and manufacturers with supply chain security requirements. These companies need cloud scale and flexibility while demonstrating to auditors that their controls are consistent across every environment, and explaining that you have different policies for cloud and on-prem is not a conversation that ends well during an audit.
Mid-market organizations without dedicated cloud security staff are particularly exposed given that research shows 45% of companies lack qualified personnel to manage multi-cloud security, a gap you can’t close in a single quarter of hiring. Without a team of cloud security specialists in-house, these organizations need a partner who can maintain a unified security posture on their behalf with guardrails that work whether they have deep expertise internally or not.
Companies modernizing gradually round out this group since not every organization can execute a big-bang migration. Some are moving workloads to cloud one application at a time over years and need a bridge that’s secure today rather than a promise that security will come together once everything is migrated. For these organizations, the security posture during the journey matters as much as the end state.
The question isn’t where. It’s how.
Hybrid done well isn’t more complex than the alternative; it’s more controlled.
Instead of managing two separate security worlds with different policies, different tools, and different blind spots, you apply one security standard across both environments, and the physical location of a workload becomes less relevant from a security standpoint because the same governance follows it wherever it runs.
This is where the industry is headed, not because hybrid is trendy but because it reflects operational reality. Data has gravity, legacy investments don’t disappear overnight, compliance requirements don’t pause for your cloud migration timeline, and performance requirements don’t bend to architectural preferences.
The companies that figure out secure hybrid infrastructure will have options: they’ll be able to move workloads where they make the most sense, run applications close to their data when performance demands it, burst into cloud capacity when they need scale, and demonstrate to auditors that their controls work everywhere. The companies that don’t will keep managing two disconnected environments, patching the seams between them, and hoping nothing slips through.
For most organizations, the question of whether to go hybrid is already answered, and what remains is whether you can build a bridge secure enough to trust.
Reach out today to create consistency in your hybrid cloud policy, or see if hybrid is right for your organization.
Q: What is hybrid cloud security?
A: Hybrid cloud security is the practice of applying consistent governance, policies, and visibility across both public cloud environments (like Azure or AWS) and on-premises data center infrastructure. The goal is to eliminate security gaps at the handoff points between environments.
Q: Why do hybrid cloud environments have more security risks?
A: Hybrid environments often evolve with different tools, teams, and policies for cloud versus data center, which creates visibility gaps and inconsistent controls. Research shows 82% of breaches in hybrid environments are attributed to this lack of unified visibility across both sides.
Q: What causes most cloud security breaches?
A: According to Gartner, over 99% of cloud security failures through 2025 will be due to preventable misconfigurations rather than platform vulnerabilities. Common causes include credential sprawl, inconsistent policies, and governance gaps between environments.
Q: How do you secure a hybrid cloud environment?
A: Securing hybrid cloud requires four things: one governance model applied everywhere, automated policy enforcement, unified visibility across all environments, and modular architecture that limits blast radius when something goes wrong.
Q: Is hybrid cloud more secure than public cloud?
A: Neither is inherently more secure. Security depends on consistent governance and visibility, not where workloads run. Organizations that apply the same policies and controls across both environments can achieve strong security posture regardless of location.
Q: Is hybrid cloud secure?
A: Hybrid cloud can be highly secure when implemented with unified governance across both environments. The security risk comes not from the hybrid model itself but from fragmented policies, disconnected tools, and visibility gaps between cloud and data center. Organizations that apply consistent controls everywhere achieve strong security regardless of where workloads run.
Q: What are the advantages of hybrid cloud?
A: Hybrid cloud lets organizations match workloads to the right environment based on performance, compliance, cost, and data location requirements. You get the elasticity of public cloud for workloads that need scale, while keeping performance-sensitive or compliance-restricted data closer to your data center. It also provides flexibility to modernize gradually rather than forcing a big-bang migration.
Q: What are the disadvantages of hybrid cloud?
A: The main challenge is complexity. When cloud and data center environments evolve separately with different tools and teams, you end up managing two disconnected security worlds. Without unified governance and visibility, the seams between environments become vulnerabilities. This is manageable with the right architecture and partner, but it requires intentional design.
Q: Who should use hybrid cloud?
A: Hybrid cloud is well-suited for organizations with significant data center investments they can’t abandon, regulated industries that need to control data location while accessing cloud capabilities, mid-market companies without dedicated cloud security staff, and organizations modernizing gradually over time rather than migrating everything at once.
Q: What is the difference between hybrid cloud and multi-cloud?
A: Hybrid cloud refers to integrating public cloud services with on-premises or private data center infrastructure. Multi-cloud means using multiple public cloud providers, such as running some workloads in Azure and others in AWS. Many organizations use both approaches, running workloads across multiple public clouds while also maintaining data center infrastructure.
Q: How do I migrate to hybrid cloud securely?
A: Start by establishing a unified governance model before moving workloads, not after. Define policies as code so they apply consistently across environments, implement visibility tools that span both cloud and data center, and architect for blast radius control so issues in one area don’t cascade. The security posture during migration matters as much as the end state.
